The injection is a command shell written in. Mutillidae can be installed on Linux Windows XP and Windows 7 using XAMMP making it easy for users who do.
Mutillidae Lesson 11 Sql Injection Union Exploit 4 Create Php Upload Script
Born to be Hacked.

. Find out how to download install and use this project. Bypass Authentication using SQL Inj ection 2012. An automated sql injection audit tool.
Brute Force Page Names using Burp -Suite Intruder 2012. A few days ago an update Mutillidae version 2117 was released. Offenders may utilize it to increase unapproved.
With dozens of vulnerabilities and hints to. SQL Injection vulnerability may influence any site or web application that uses the SQL database for example MySQL Oracle SQL Server or others. In Mutillidae go to OWASP 2017.
Ethical Hacking - SQL Injection. SQL Injection is a code-based vulnerability that allows an attacker to read and access sensitive data from the database. In this video learn.
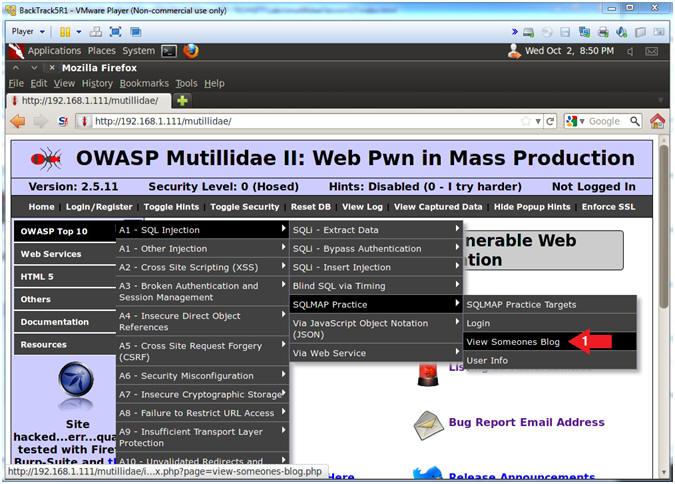
SQL injection is a set of SQL commands that are placed in a URL string or in data structures in order to retrieve a response that we want from the databases that are connected with the web applications. OWASP Mutillidae II is a free open-source deliberately vulnerable web application providing a target for web-security training. X SQL injection can be employed to become the administrative user or a user of the attackers choosing Figure 1 Druin Mutillidae.
To learn how an attacker might go about compromising an. You signed out in. The server is fully patched with anti-virus running and a firewall blocking port 23.
Find out how to download install and use this project. SQL Injection Causes Simply stated SQL injection vulnerabilities are caused by software applications that accept data from an untrusted source internet users fail to properly validate and sanitize the data and subsequently use that data to dynamically construct an SQL query to the database backing that application. Using somewhat advanced SQL injection we inject a new PHP file into the web root of the PHP server using and SQL injection vulnearbility in Mutillidae.
Reload to refresh your session. The existing version can be updated on these platforms. Attackers can bypass security measures of applications and use SQL queries to modify add update or delete records in a database.
The Metasploitable server provides a Mutillidae web application which is vulnerable to SQL injection attacks. This cheat sheet gives a quick overview of uses and syntax for multiple cases various DBMS and URL. In this example we will demonstrate how to detect SQL injection flaws using Burp Suite.
Add to your blog. This tutorial uses an exercise from the Mutillidae training tool taken from OWASPs Broken Web Application Project. SQLMap is the standard in SQL Injection.
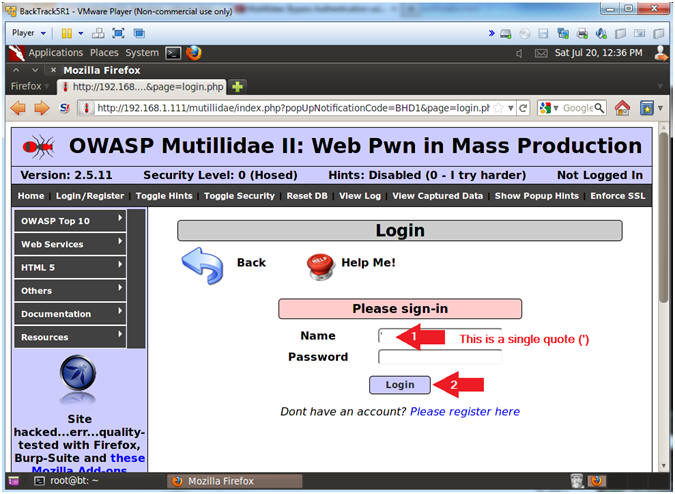
Enter the below-mentioned command in the vulnerable field and this will result in a successful Authentication Bypass. A1- Injection SQL. Type in a single quote in the input text area and submit.
This should generate an error at the top of the page that gives you sight of the SQL INSERT statement. In this video a Windows web server is hosting Mutillidae web application which contains a command injection vulnerability. For demonstration purposes we will use metasploitables Mutillidae web application which is vulnerable to SQL Injection attacks.
It is pre-installed on SamuraiWTF and OWASP BWA. After we confirm that the site is vulnerable to SQL injection the next step is to type the appropriate payload input in the password field to gain access to the account. Using command injection to exploit the Mutillidae web application we gain a root shell Administrative Windows cmd shell.
If you take a user input through a webpage and insert it into a SQL database there is a chance that you have left yourself wide open for a security issue known as the SQL InjectionThis chapter will teach you how to help prevent this from happening and help you secure your scripts and SQL statements in your server side scripts such as a PERL Script. Contribute to harryct229mutillidae development by creating an account on GitHub. This type of attacks generally takes place on webpages developed using PHP or ASPNET.
Click on Mutillidae link. This is done by including portions of SQL statements in an entry field in an attempt to get the website to pass a newly formed rogue SQL command to the database eg dump the database contents to the attacker. The video walks through using sqlmap to locate an sql injection determine the backend database type enumerate the database account databases schema tables columns and password hashes then use the database to.
You signed in with another tab or window. A successful SQL injection attack can badly affect websites or web applications using. Using this access an attacker can retrieve information from the database in an unauthorized way especially from those tables that arent typically accessible by users.
OWASP 11 Vulnerable Applications Almost all SQL databases and programming languages are potentially vulnerable. Recorded at the ISSA Kentuckiana February 2013 Workshop this video review the use of sqlmap. Mutillidae 2117.
Mutillidae is a free open source web application provided to allow security enthusiest to pen-test and hack a web application. SQLi Insert Injection. Inserting Data with SQL injection.
SQL injection also known as SQL fishing is a technique often used to attack data driven applications. This tutorial uses exercises from the DVWA WebGoat and Mutillidae training tools taken from OWASPs Broken Web Application Project. Now Go to OWASP 2017 A1 Injection.
To check for potential SQL injection vulnerabilities we have entered a single quote in to the Name field and submitted the request using the Login button. X Administrative pages may also be reached by brute forcing the page name 16 Druin Mutillidae. Inject Root Web Shell Backdoor Via SQL Injection.
A lot of the tutorials demo templates are vulnerable Even worse a lot of solutions posted on the Internet are not good enough In our pen tests over 60 of our clients turn out to be vulnerable to SQL Injection. A SQL injection is a type of vulnerability that gives users access to the database associated with an application allowing them to execute SQL queries. Mutillidae can be installed on Linux and Windows using LAMP WAMP and XAMMP.
Other Injection Frame Source Injection Document Viewer Using Setoolkit to clone Login page of mutillidae 2 Web Attack Vectors - 3 Credential Harvester Attack.
Mutillidae Lesson 12 Sql Injection With Sqlmap Tamper Data Burpsuite

Learning By Practicing Beginning Web Application Testing Sql Injection Mutillidae

Know How To Start Learning Hacking Blind Sql Injection For Forms Fields Using Sqlmap

Sql Injection In Mutillidae What Is Sql Injection By Tanvi Trivedi Medium

Sql Injection In Mutillidae What Is Sql Injection By Tanvi Trivedi Medium

Lab5 2 Part 1 Sql Injection On Mutillidae Youtube
Mutillidae Lesson 5 Manual Sql Injection With Firebug

Learning By Practicing Beginning Web Application Testing Sql Injection Mutillidae
0 comments
Post a Comment